Table of contents
- Background - what's a Jailbreak
- Motivation - why and who cares
- Implementation - jailbreak detection methods
- Concerns - how accurate is Jailbreak Detection
- Evaluation - is it worthwhile to have Jailbreak Detection in 2023
- Stats: jailbreak vulnerability for devices running iOS 16
- Question - what alternatives exist?
In this blog post, I'll show what detection methods exist and share code examples. But more importantly, I'll discuss the motivation for jailbreak detection, share related implementation, and present information so that you assess if jailbreak detection is a good idea in 2023 (or in general).
Background - what's a Jailbreak
Jailbreaking is the use of a privilege escalation exploit to remove software restrictions imposed by Apple by
modifying the operating system (enforced by a "locked bootloader")
installing non-officially approved applications (known as "tweaks") via sideloading utilizing package managers such as Cydia or Sileo
granting the user elevated administration-level privileges (rooting)

"Virtual" jailbreaks are nowadays often advertised but are scams!
Motivation - why and who cares
Stakeholders of enterprise apps are concerned that the missing sandbox restrictions on a jailbroken device can be exploited by tweaks and comprise the security level of their apps.
Apps with sensitive or valuable data are therefore often required, by their stakeholders, to implement jailbreak detection to increase security.
The OWASP MASVS (Mobile Application Security Verification Standard) is the industry standard for mobile app security. Its purpose is to be used by mobile software architects and developers seeking to develop secure mobile applications, as well as security testers, to ensure completeness and consistency of test results.
The very first requirement concerning resilience, MSTG-RESILIENCE-1, reads as follows:
The app detects, and responds to, the presence of a rooted or jailbroken device either by alerting the user or terminating the app.
Implementation - jailbreak detection methods
I recommend reading this good article about Jailbreak Detection Methods.
Filesystem-based Detection
API-based Detection
OpenSSH Service Detection
Cydia Scheme Detection
Various code examples can be found in the MASTG, including this one.
do {
let pathToFileInRestrictedDirectory = "/private/jailbreak.txt"
try "This is a test.".write(toFile: pathToFileInRestrictedDirectory, atomically: true, encoding: String.Encoding.utf8)
try FileManager.default.removeItem(atPath: pathToFileInRestrictedDirectory)
// Device is jailbroken
} catch {
// Device is not jailbroken
}
A well-maintained, BSD 2-Clause licensed implementation, reusable as a Swift package, can be found on GitHub.
The simplest method returns true or false if you want to know if the device is jailbroken or not.
if IOSSecuritySuite.amIJailbroken() {
print("This device is jailbroken")
} else {
print("This device is not jailbroken")
}
There is also a more verbose API to know what indicators were identified.
let jailbreakStatus = IOSSecuritySuite.amIJailbrokenWithFailMessage()
if jailbreakStatus.jailbroken {
print("This device is jailbroken")
print("Because: \(jailbreakStatus.failMessage)")
} else {
print("This device is not jailbroken")
}
The failMessage is a String containing comma-separated indicators.
Example: Cydia URL scheme detected, Suspicious file exists: /Library/MobileSubstrate/MobileSubstrate.dylib, Fork was able to create a new process
Concerns - how accurate is Jailbreak Detection
There are popular iOS jailbreak detection bypass tweaks such as A-Bypass, Not a bypass, Shadow, and others.

Such tweaks anticipate that Jailbreak detection implementations will perform certain checks and try to fake results.
Common bypass tweaks often do not work on specific apps and attackers might need to create/use bypasses made specifically for a certain app.
I tested on a jailbroken iPad Air 2 running iOS 15.7.3 and verified that the open-source implementation protects an app against the following bypass teaks
A-Bypass
Choicy
Hestia
Not a Bypass
A jailbreak detection implementation might use FileManager to detect if a file directory can be accessed that normally is not, e.g. /var/log/syslog. If true then Apple's sandboxing system is comprised and the app runs on a jailbroken device.
A jailbreak detection bypass tweak might hook into FileManager and return false to hoodwink you.
For a more comprehensive example, including how to analyze jailbreak detection within an iOS app, I recommend the following article:
Bottom line: jailbreak detection can ALWAYS be reversed-engineered and evaded by DEDICATED attackers
Evaluation - is it worthwhile to have Jailbreak Detection in 2023
The increased feeling of security, at least against common detection bypass tweaks, comes with a price tag.
Ongoing efforts to research and update the detection implementation are needed to protect against the common bypass tweaks.
Ongoing costs to obtain and maintain test devices for the sole purpose of jailbreak detection.
I cannot tell you if the efforts are justified for your business case. What I can share is some current numbers so that you can quantify the threat level.
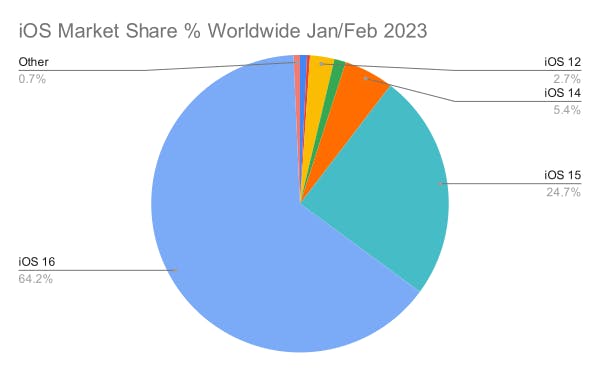
Stats: jailbreak vulnerability for devices running iOS 16
As of February 2023, the latest major iOS release (= 16) has approximately ~ 64% market share worldwide.
Only 10 out of the 46 devices compatible with iOS 16 can be jailbroken:
iPhone 8, 8 Plus, and X
iPad 5-7, iPad Pro 9.7-inch, 10.5-inch, 12.9.-inch (1st & 2nd gen)
That is due to the unpatchable checkm8 exploit, found in the Bootrom of Apple’s chips from A5 to A11 Bionic, and the folks behind the Palera1n jailbreak that leverages the exploit.
I was able to jailbreak my iPad Air 2 device running iOS 15.7.3 within a day with Palera1n but had to do a factory reset of the device first.
Determine whether a public jailbreak is available for your version of iOS
Question - what alternatives exist?
Apple introduced a new feature called App Attest with iOS 14.
This feature, part of the DeviceCheck framework, aims to reduce the inappropriate use of developer servers through compromised apps and minimizes the risk of unauthorized features like "game cheats, ad removal, or access to premium content".
You can sign server requests to prove to your server that they came from an unmodified app version.
It's important to know that App Attest is not a "is this device jailbroken?" check, as that has been proven over and over to be impossible to pinpoint. Instead, it aims to protect server requests in order to make it harder for hackers to create compromised versions of your app that unlock premium features or inserts features like cheats [...] Note the word harder: as jailbreakers have physical access to their devices, nothing will completely safe-guard you from fraud in this case.
Apple does note that "no single policy can eliminate all fraud," and adds that App Attest isn't able to pinpoint a device with a compromised operating system.